
Your brain is constantly working to detect threats to your safety–whether you realize it or not. When visiting an unfamiliar place, your senses take in stimuli, which your brain uses to protect you. For enterprises, defensive cybersecurity systems have the same goal. One such system making waves in information security is the Zero Trust Network (ZTN). ZTNs gather information and assess risk to protect your business’s network and data.
Using a ZTN, your company can employ the same process of collecting information to ensure protection against cyberattacks. It can be challenging to know where to begin when looking to improve your company’s cybersecurity mechanisms. OnX security services can equip your organization with the support you need to identify and manage threats across your network.
This blog will examine the functions and importance of ZTNs in enterprise cybersecurity.
What are the threats to your information, your users, and your vendors?
Today, many companies provide network access to users, vendors, and customers. Establishing a secure, private network with features like a VPN is vital to protect your network and outside devices, users, and vendors.
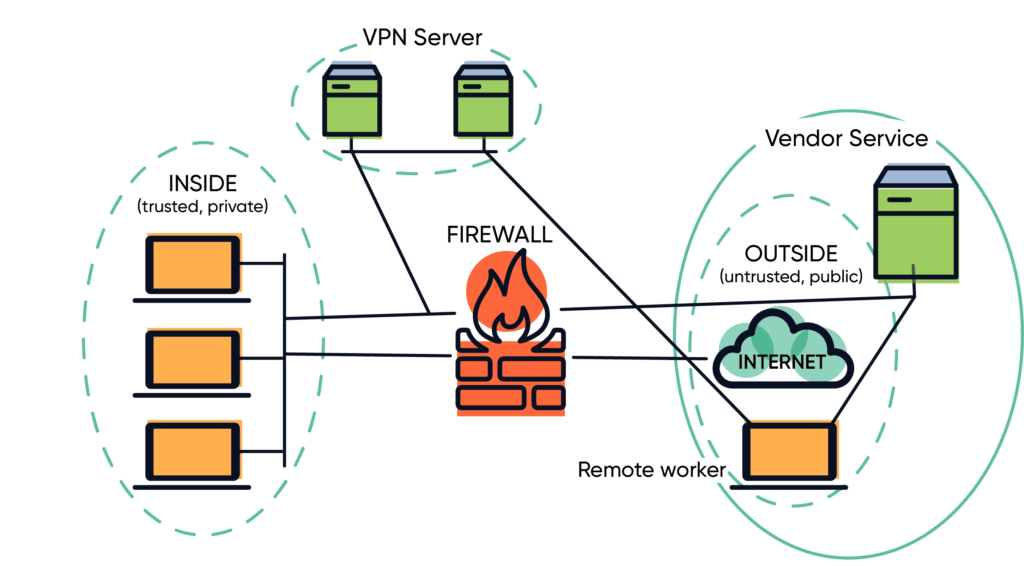
A well-designed security framework is critical to protecting your network and those accessing it against cyberattacks. Load balancers, DMZ, cloud services, web application firewalls, and more can all be added to the environment for added complexity where needed. Modern networks have three primary threat vectors.
- Compromised user credentials can be used to access your network or your vendor’s network.
- A compromised device on your internal network, your vendor’s network, or the remote network can expose your company or vendor(s) to an attack.
- A compromised software system—such as an API—can impact or infect data on your network, the vendor’s network, or the remote network.
For any modern network, there are an exponential number of risk factors. Each device and vendor that accesses your network creates a new potential threat not only for your internal network, but for all users and vendors who access it. With data and systems now distributed among on-premises data centers, cloud providers, and work-from-anywhere employees, perimeter defense is no longer enough to protect your business assets. How can you leverage a Zero Trust Network to establish trust between devices and diminish possible threats?
How a Zero Trust Network protects your business
The basis for a Zero Trust Network is the requirement to provide credentials, validate them, and then check for authorization. Rigorous authentication steps are applied to all internal and external users and devices trying to access the private network. User authentication is a critical aspect of network security because once an attacker is inside the network, they can easily move around among assets. Trust nothing, verify everything.
The first step is to determine who and what devices are accessing your network. This information will help you analyze possible threats and the trustworthiness of each device and user. It’s essential to treat all devices and users as strangers–even assets you might otherwise trust, such as your own workstations.
Imagine a network configuration that doesn’t trust any computer, user, or process until it provides credentials (such as a username and password or X.509 certificate) and can validate its authenticity with a second factor. Examples of a second factor include an SMS text, authenticator push, or security certificate. After determining identity and authorization, the network can assign a security certificate to a device, a user, or a program, allowing access to the network. The ZTN continuously verifies its users and devices, only permitting access to the specific resources they need.
Establishing trust between devices and users
When authenticating a device, IP addresses are unreliable measures of “identity,” so the machines themselves must be validated before issuing a certificate. Some solutions automate this process and gather context to determine if the network recognizes the device. Context, in this case, can mean the MAC address, serial number, or IP address. The more information you have about a device, the more confidence you can have that the device is trustworthy. As an added security measure, the trust and certificate extended to any device only lasts for a single session or for a predetermined length of time.
Users have to be validated twice because a username and password aren’t a strong indicator of the user’s authenticity. The network can confirm the user’s identity through multi-factor authentication (MFA). MFA uses an SMS or an authorization application like Duo or Microsoft Authenticator to provide a level of trust that the user is who they say they are. MFA is one of the most critical defenses your company can put in place. User authentication, like device authentication, lasts for a single session or a predetermined amount of time, and the user will need to re-authenticate once they disconnect.
There are many other ways a Zero Trust Network can benefit your company. For example, as your cybersecurity program progresses, you can verify the applications or software running on your systems. Your network would accomplish this by using lists of the network’s trusted applications and a hash value of the executables to ensure that the application in question has not been modified. It’s a complicated process, but it is possible.
Ready your security systems to take on the modern era
Today, enterprises face more threats and vulnerabilities than ever. Implementing a Zero Trust Network is the first step to strengthening your security systems. Based on your unique security goals, you might choose to hold off on upgrading your VPN and consider investing in a ZTN solution for your workforce.
OnX’s security solutions are designed to keep your data safe and reduce costs. By partnering with OnX security experts, you can take advantage of:
- 24x7x365 enterprise-class monitoring.
- A complete set of solutions for your IT security requirements.
- The ability to scale quickly and on-demand.
Contact the OnX cybersecurity team today for help assessing and improving your company’s cyber defense.
More from John Bruggeman:
Strengthen your cybersecurity defenses with the MITRE ATT&CK Framework
How CIS controls can simplify cybersecurity
Ransomware-proof your enterprise with Canada’s ITSG-33 security framework
















