
The best value of deploying applications in a multi-tenant or public cloud is speed and simplicity. Your cloud provider can have your applications deployed and running within hours if not minutes once automated. However, with simplicity comes the risk of exploitation. There are various techniques that can be leveraged to secure applications. Below are a few simple steps that can be layered into any application deployment for multi-tenant or public cloud.
Deploy the application to the users
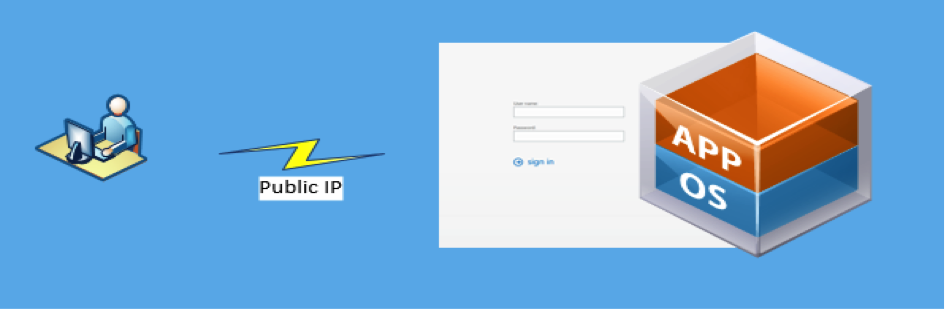
Let’s start with a web application deployed on a single virtual instance. Most cloud providers will auto assign a public IP from a shared pool. Traffic to these IPs are considered unfiltered without any logical isolation of traffic.
Firewalls and Filtering
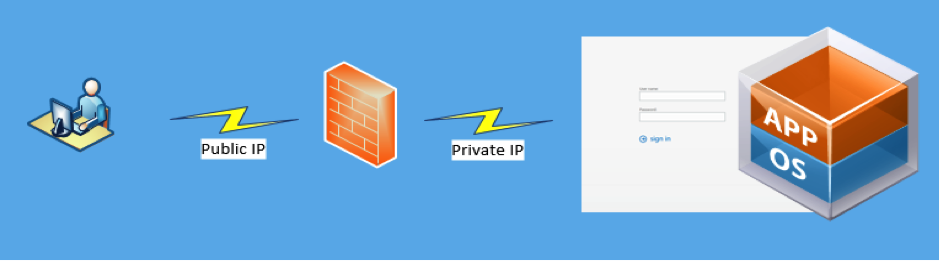
Depending on your cloud provider the features provided by the firewall will vary. You can also choose to deploy a variety of virtual firewall appliances either commercially available or via the open-source community. Things to consider when deploying a virtual firewalls appliance:
- Stateful packet inspections
- VPN Tunnels
- Bandwidth throttling
- Intrusion detection and prevention (IDS/IPS)
- Quality of Service (QoS)
- Network Address Translations (NAT)
- Access Control Lists
Using Web Proxies and Web Caches
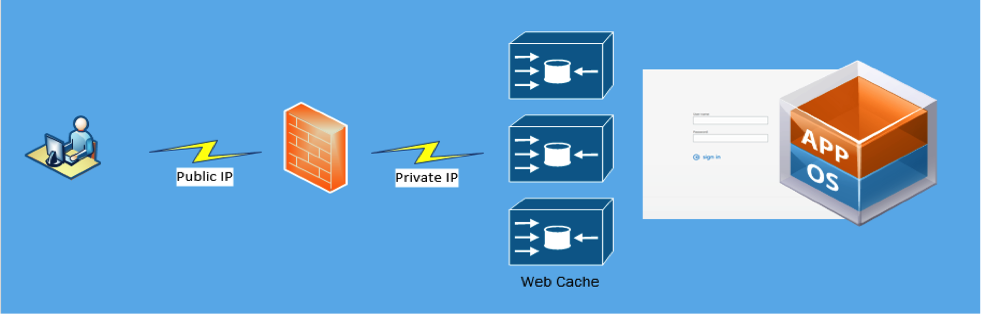
Adding a web cache and proxy in-front of the application is a common security practice when adding security using defense in depth. Clients do not connect directly to the application servers but instead connect to the proxy. Here is a very good opportunity to start offload workloads and increase client connection response times as more proxies are added. Let’s not forget about the unwanted connections as these attacks will be directed to the proxies and isolated to the proxy/cache layer.
Monitoring and Log Management
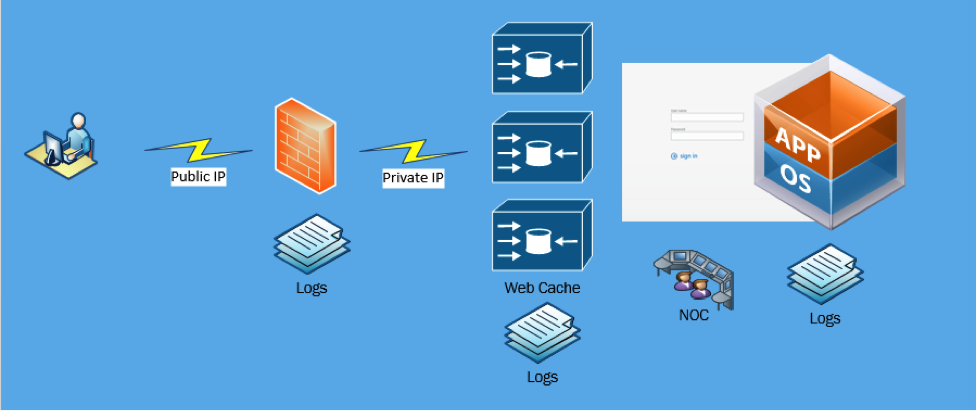
There is nothing worse in the world of infrastructure management than being the last person to know your systems are down or functioning incorrectly. As more applications are deployed and more instances created there should be monitoring services deployed on these instances sending notification to your 24×7 Support Staff or Network Operation Center. There are also a growing number of Security information and event management (SIEM) services available that provide automated algorithms for threat management, compliance and automated incident response.
Data Encryption
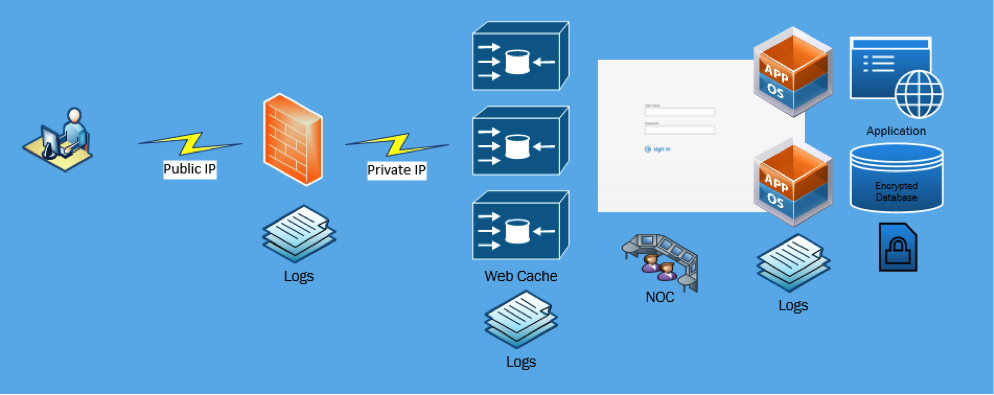
Finally as with any application deployed with a cloud provider and data stored outside of the traditional corporate building, it is best to have that data encrypted. After mitigating any type of logical data breach using isolation, restriction and layered defense – encryption ensures that any data acquired as a result of physical access will be unreadable.
While most businesses do a pretty thorough job of planning and researching IT security, the planning and budgeting for the operationalization of the new IT security purchase is often forgotten about. To find out more about our Security Services, download our FREE guide:
















